Tips How to Secure Windows and Powershell
The content from this article is based on an learning course from LinkedIn named Powershell:Securing Windows Environment.
Enable poweshell user login using GPO
Enable Policy on GPO
Create a new GPO to enable powershell logging.
[GPO]--> Computer Cofiguration > Adminstrative Template : > Windows Components > Windows Powershell.
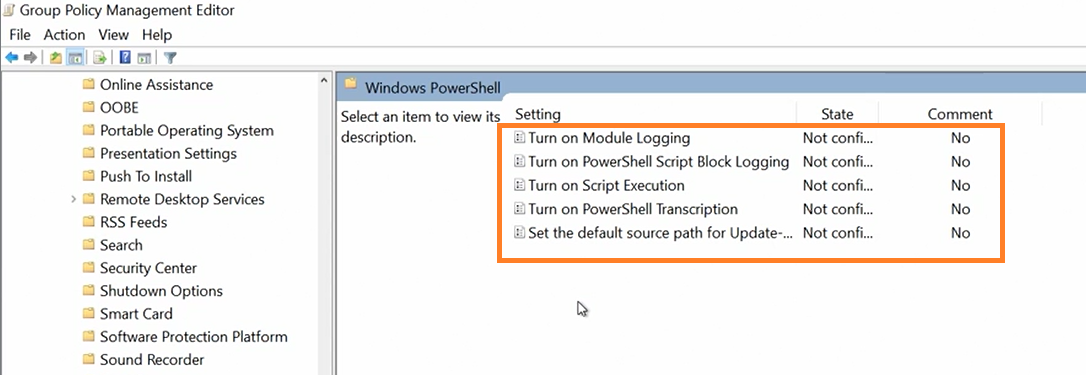
Logging Activity
There are four components that we can turn on loggin for powershell,using regedit or group policy we can view them under event viewer.
- Audit logs for suspicious activity
- Transcript
- Scriptblock
- Module
Enable(OTS) Over-the-Shoulder transcription
Enable this Regedit by changing its value to 1
Also change the output directory for the file path.
Local Machine> Software > Policies > Microsfot > Powershell > Transcription
Module Logging
This will be useful to log when scripts.ps1 are run on the system, the events will be capture on Windows powershell event logs.
Of course you can enable the transcript to be saved in a share folder, or server log. This will make much harder for an attacker to delete their footprint after running their malicious pre.
Run the below conmmand to view the last 15 powershell command logged by the Windows powershell
Get-WinEvent -Logname "windows Powershell" | Select -first 15 | out-Gridview
Location Obfuscation
An encoded command will be a command often written in Base64 or binary example:
powershell -eNco ZQBjAGgAbwAgACIAVwBpAHoAYQBVyAGQAigA=
There is not build in defense for this kind of attack , however there is a good module you can use to parse powershell logs.
Use the Poweshell module DeepBlueCLI to parse Security,Events and Powershell .evtx files, it will automatically detect the execution of base64 when parsing the logs by using RegEx, and also detect other common security events.
Disable powershell 2.0
Powershell 2.0 is a deprecated version of powerhell, and was left as a component on Windows to make powershell redundant to older applications.
If you’ve developed/running an application with .NET 2.0/3.5 (aka CLR2), and you’re hosting
a PowerShell assembly like System.Management.Automation.dll, then you’re using the Windows PowerShell 2.0. Which in this case
you will need to have powershell 2.0 enabled and it might be a good idea to keep it on actually.
In order to continue to have your application running, or migrate to .Net 4.6+
To verify if we have it enbabled on our system run the below command.
Get-WindowsOptionalFeature -Online -FeatureName MicrosoftWindowsPowerShellV2
On a Windows server run the below
Get-WindowsFeature PowerShell-V2
Powershell Remote Management
The chances are that you will need this option enabled on most server you deploy, however, if you are not using
maybe its a good ide to turn it off.
- Turn the Services.msc OFF - WIndows Remote management (WS-Management)
- Add an explicity rule on Firewall to block traffic on 5985 & 5986
The following ports are used for Windows Remote Management WMIC
- HTTP:5985
- HTTPS:5986
These are common ports used for management of computers over the network, and they are open by default
if you are using network share drivers.
If we need to close these ports we just need to create an inboud rule on FireWall
This is not recommended for the long term as there are many Administration and applications relly on powershell remoting.
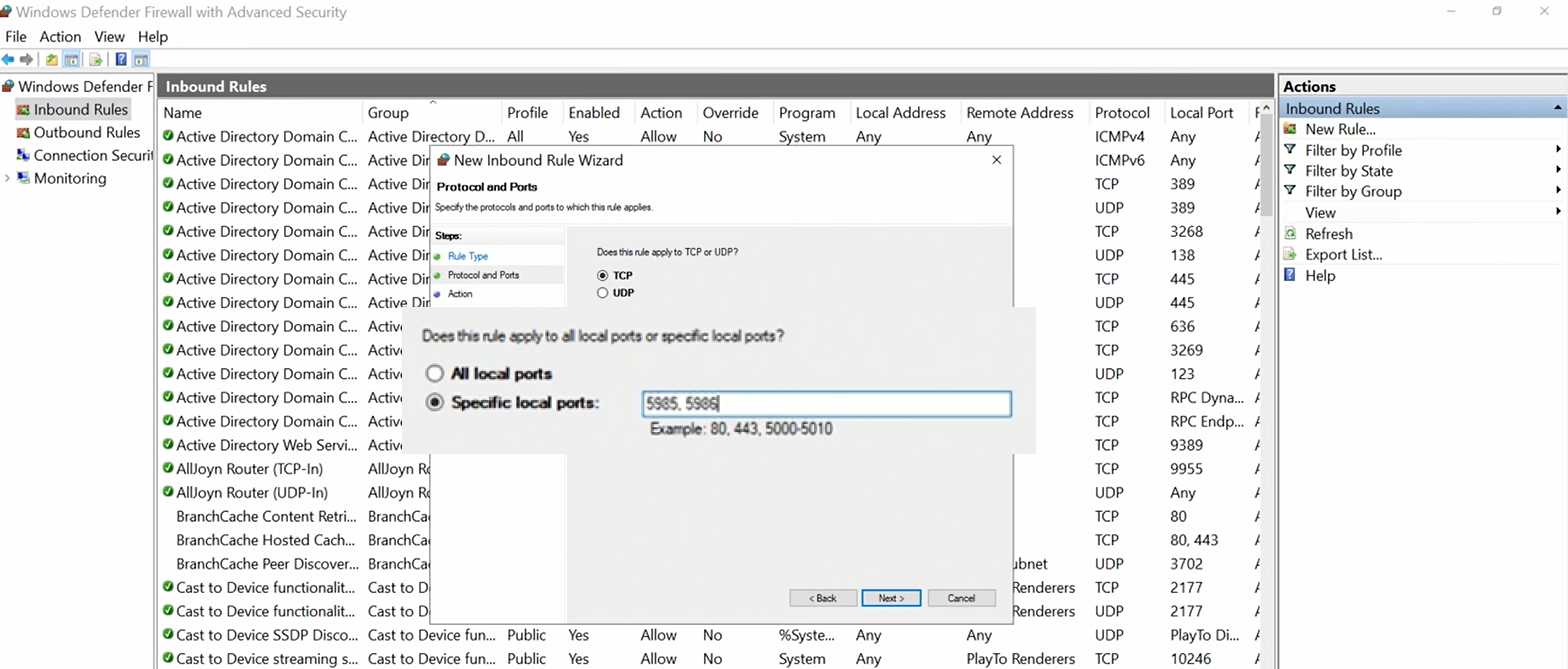
Change Default Port for WMIC
One way to add security to WMI is to change the default port number we are using, so intstead of using HTTP:5985 and HTTPS:5986 we use something different like 6005. Run the below command on the local machine to change
Set-Item wsman:\localhost\listener\listener*\port value 6005
Client runs below to connect
Then from the client computer initiating the connection we need to specify the correct port to use, to find the correct port the server is listening from.
New-PsSession -Computer [ComputerName] -port 6001
Enter-PsSession [SessionID]
Windows Defender Capabilities
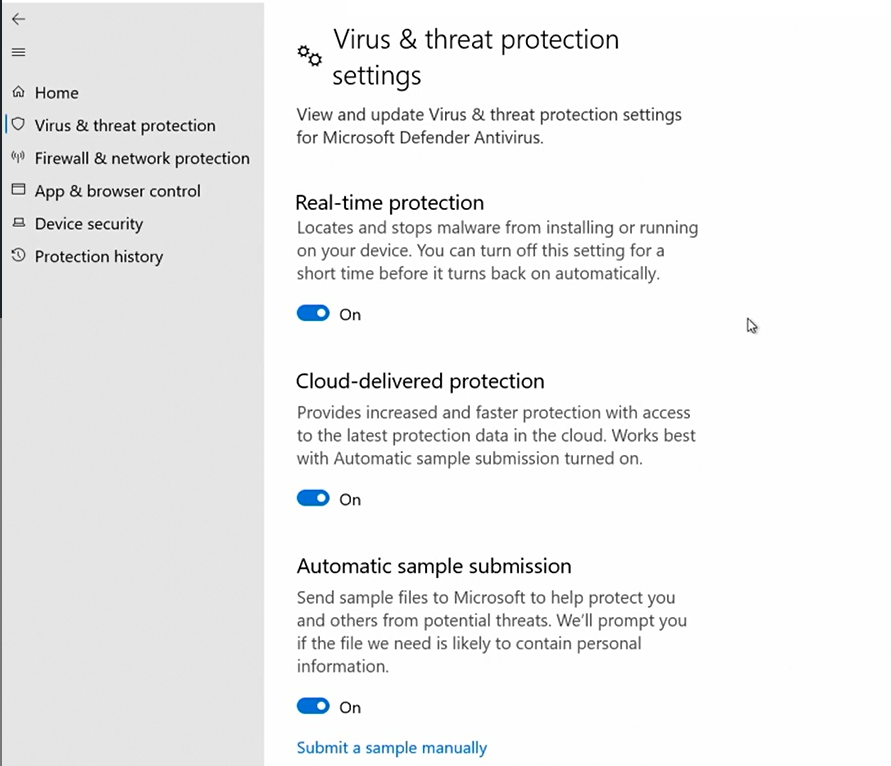
You do want to keep your server updated, even if its airGapped (offline), to help you achieve that make sure you have a way to send Security Updates to your server, or its pulling updates directly from a relay server inside your DMZ zone.
We also want to enable Real-time protection which is turned off by default, and this will scan files as they are being openned for any sign of malware.
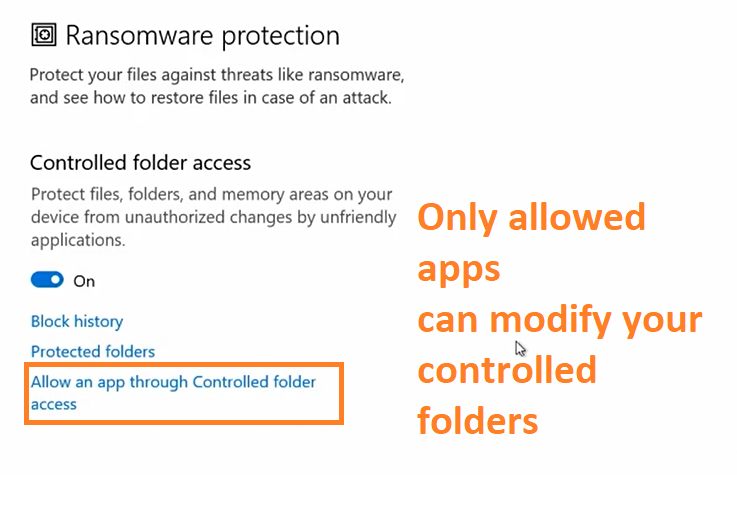
Control folder access
We can control which folders are not to be messed with, so it will protect files, folders and memory areas.
This is a good protection against Ransomware as these folder will be prevented from being encrypted or altered.
If you have an app that needs to read/edit those files you need to allow the app explicitly to have permissions to modify the folders
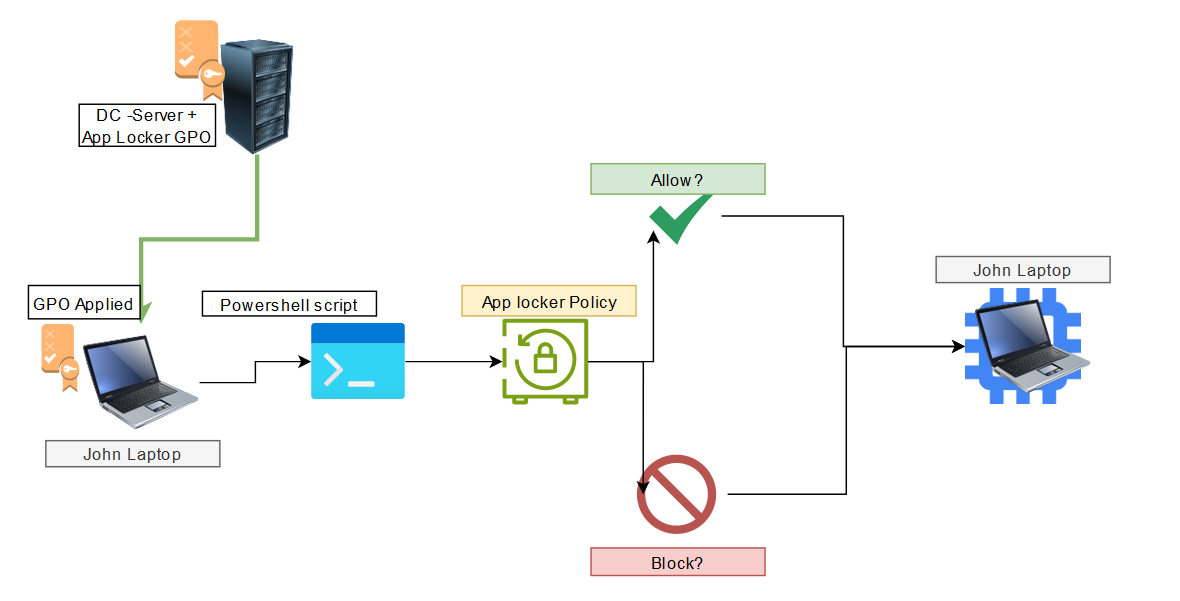
Secure Poweshell with AppLocker
When we enable AppLocker, whenever a powershell script is run it will perform a check against appLocker, to make sure it is enabled
to run on the target system. If the script is allowed either by its (Hashfile, Publisher,or file/path) then the script will run normally,
otherwise the script will be blocked. Below is a diagram on how this is working behind the scenes.
AppLocker can also perform checks against plugins, add-ins, and modules that can run from specific apps.
We could restrict powershell usage using app lock, however,because most of us have scripts that are run either for HealthChecks, or other performacing tasks can sometimes not be very effective if implemented poorly.
[GPO]-->Application Control Policy > App Locker > Configure Rule Enforcement
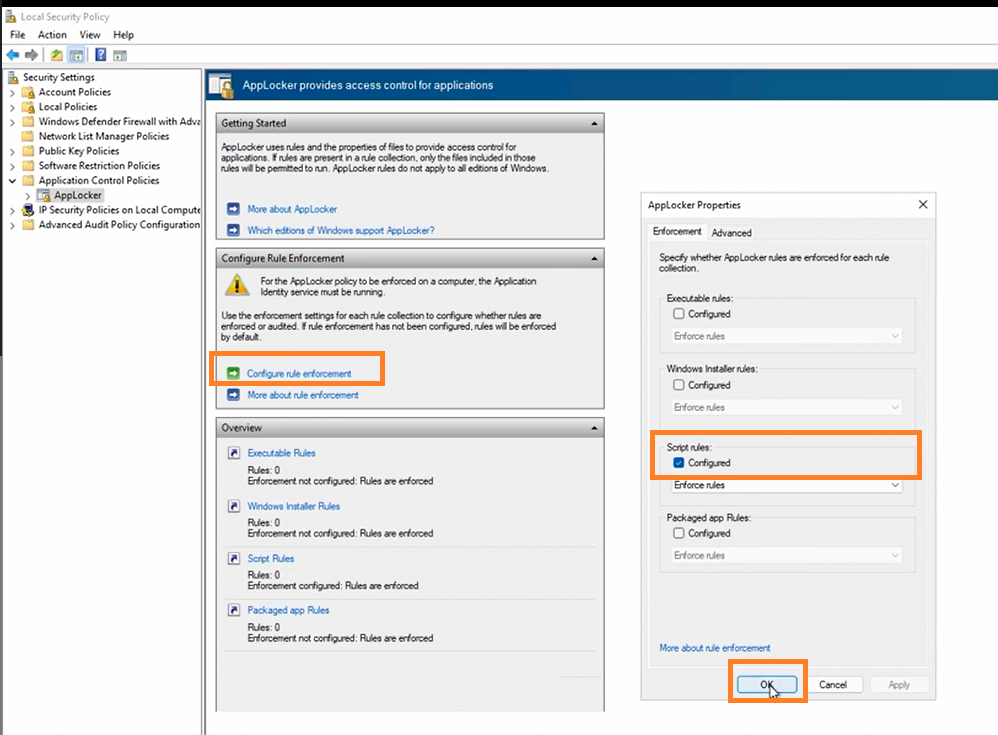
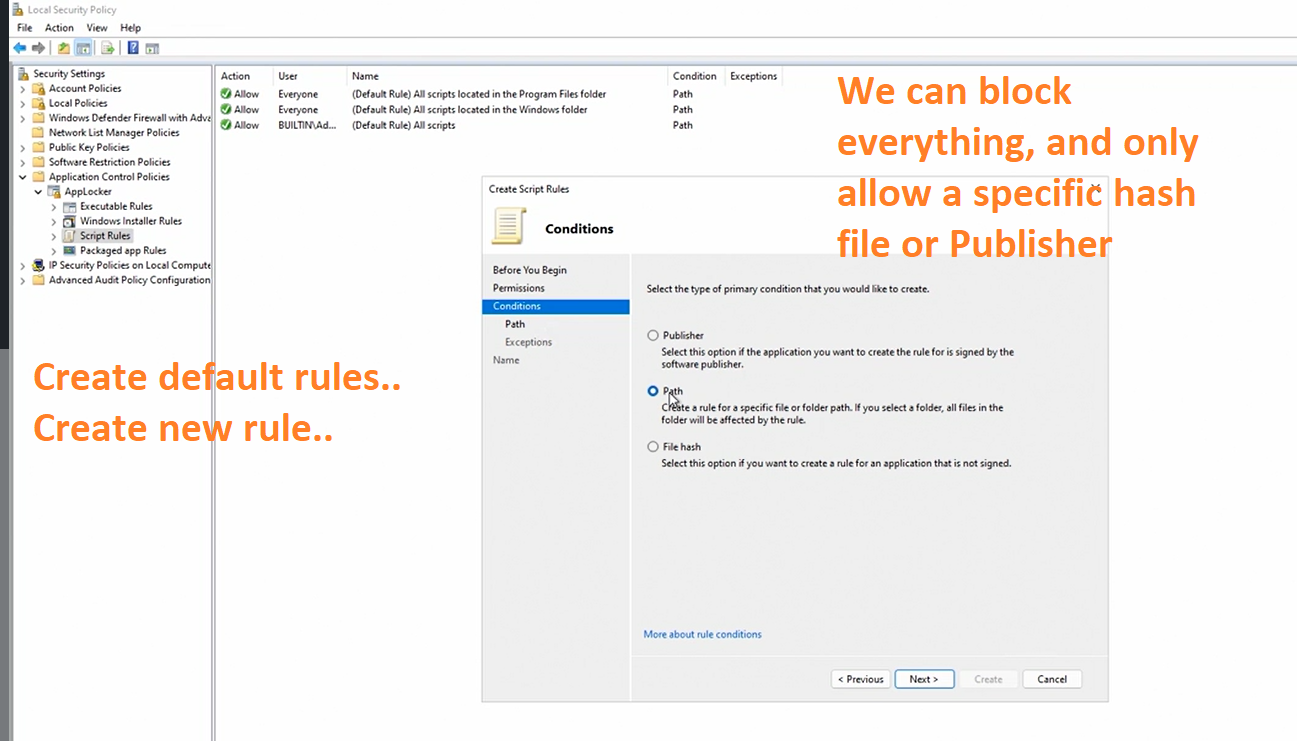
We could potentially block all powershell script usage across the whole computer and only allow certain file hashes or Publisher to Run scripts on our network. If we are running a KPI server that can handle certificates to developers this will be great tool to add to our security posture.
With the KPI Server the developer will be able to sign the scripts with a certificate, the certificate the endpoint device will recognize this certificate as trusted and be able to run the script.
Powershell constrain languages models
The below command will restrict what command can be run on powershell, it can run functions, cmd-lets, variables but no script blocks A similar configuration to Language restriction would be the use of JEA(Just Enough Adminstration)
$ExecutionContext.SessionState.LanguageMode = "ConstrainedLanguage"
Poweshell language restriction is best applied on users who do not need powershell for their daily work.
(JEA)Just Enough Admministration
JEA, provides a way to limit the commands that can be run by specific users.
We can control specific cmd-lets to be used, and parameters that are accepted.
JEA runs on a sandbox powershell remote session and extrict limit what an user can do. Everything is controlled by a
language file which is store on the server and act as a configuration file
Powerhell Execution Policy
This is the policy that will control the execution of powershell scripts on your local computer.
- Restricted
- AllSigned
- RemoteSigned
- Unrestricted
Restricted
No powershell scripts will be run on the system. - Most restricted, most secure.
AllSigned
All scripts need to be signed, by a trusted (CA)Certificate Authority
RemoteSigned
Scripts that are written by you on your local computer will run, but scripts you download from the internet will not run
Unrestricted
All scripts will run freely on your computer. - Most persmissive, least secure.
Summary
There are other methods you can use to secure your endpoint, please be mindful that we are not talking about on this article how to protect your endpoint using 365 Defender or Azure policies or other mechanism, however, I would recommend searching for articles on those as well.
For more information on how to keep your Widows Machine secure, make sure to check the Cyber Samurai every now and then.
.png)