Better protecting our assets
Understanding the traffic on our network is essential in order to build a secure environment. Having visibility of what protocols are being used will give us information if any computer is running a cryptocurency mining activity or maybe an instant message app.
Tools for Network Sniffing
- Wireshark
- TCPDump
- Ettercap
- Dsniff
Tapping into wireless will act like a hub and allow to see all traffic
Tapping into a wired network we will likely hit a switch a only see our own traffic, broadcast and multicast traffic.
Vulnerable Layer 2 Protocols
Firewall and IDS services normally work on the network layer (layer 3 - IPs) or above, leaving the data layer, (layer 2 - MACs) exposed.
Below are some layer 2 protocols that are vulnerable, and many are related to CISCO devices
Vulnerable Layer 2 Protocols
- STP - Spanning Tree Procol
- CDP - Cisco Discovery Protocol
- DTP - Dynamic Trunking Protocol
- DHCP - Dynamic Host Configuration Protocol
- HSRP - Hot Standby Router Protocol
- ISL - Inter-Switch Link
- VTP - VLAN Trunking Protocol
- 802.1Q - Vlan Tagging protocol
- 802.1X - Authentication WiFi
Attacking
A build in tool on Kali we can use to perform this type of attack on layer 2 protocols is Yersinia
sudo yersinia -G
Legal and Illegal capture
First we need to understand that are two methods of capturing traffic over the network, that is the Legal method and Illegal method
The legal method is either configure by the System Administrator on the switch and will forward or send a copy of the traffic for analysis into a different administration port.
Methods include:
- SPAN - Switch Port Analysis
- Port Mirroring
How Attackers Sniff Traffic
Sniffing can also be done by other methods of capture, like MAC spoofing, or IRDP Spoofing, or applications like WireShark, below we will look at some of these attack methods deployed by threat actors and how to defend against them.
Spoofing Attacks
MacOf Attack
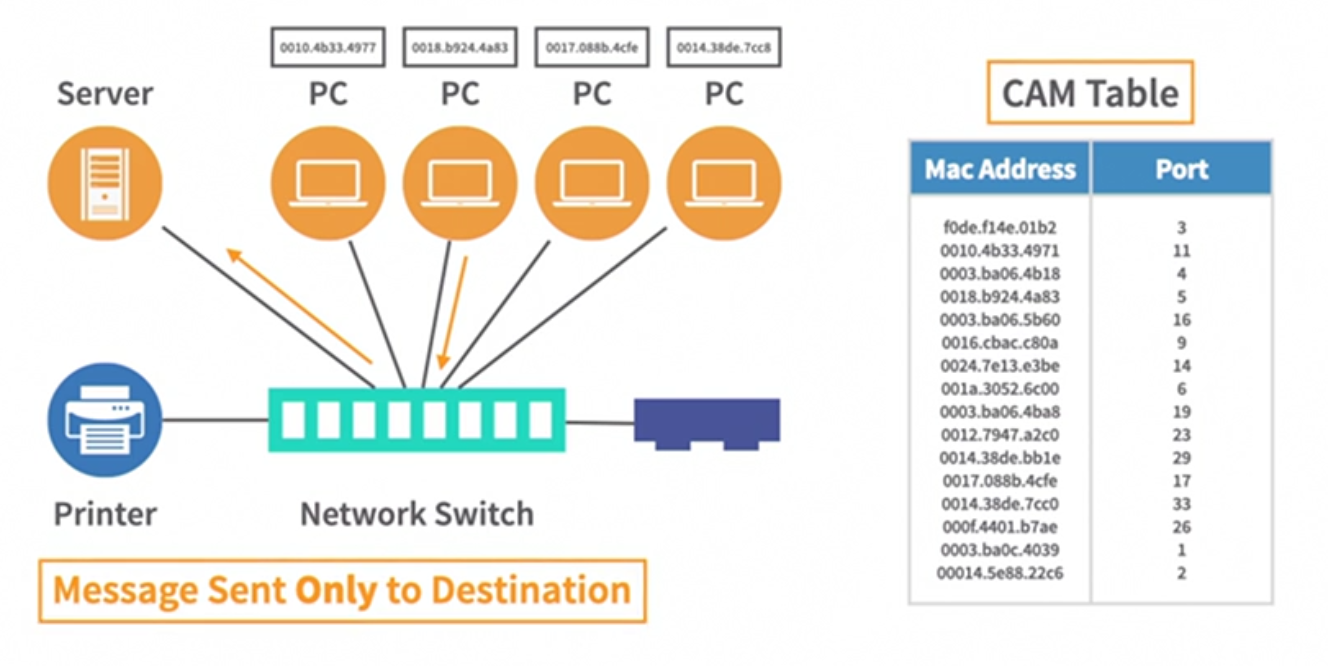
MacOf is an MAC overflow This attack floods the CAM table of the switch, so the switch start behaving like a hub sending data to all ports.
Attacking!
Kali Linux has a build in tool for this type of attack
sudo macof
The attack must continue to flood the switch for it to work, When the attack stops the switch will revert back to being a switch.
If attack is successful
- Switch will behave like a hub
- Do nothing - has protection enabled
- Crash and reboot
Defending
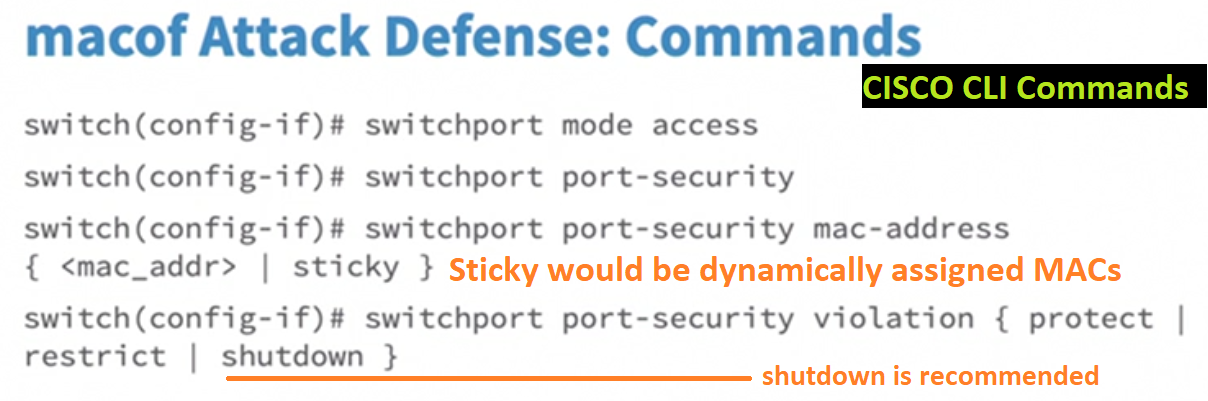
On a switch, use switchport security, this limits the number of MAC Address connecting to a single port on a switch.
Arp Spoof Attack
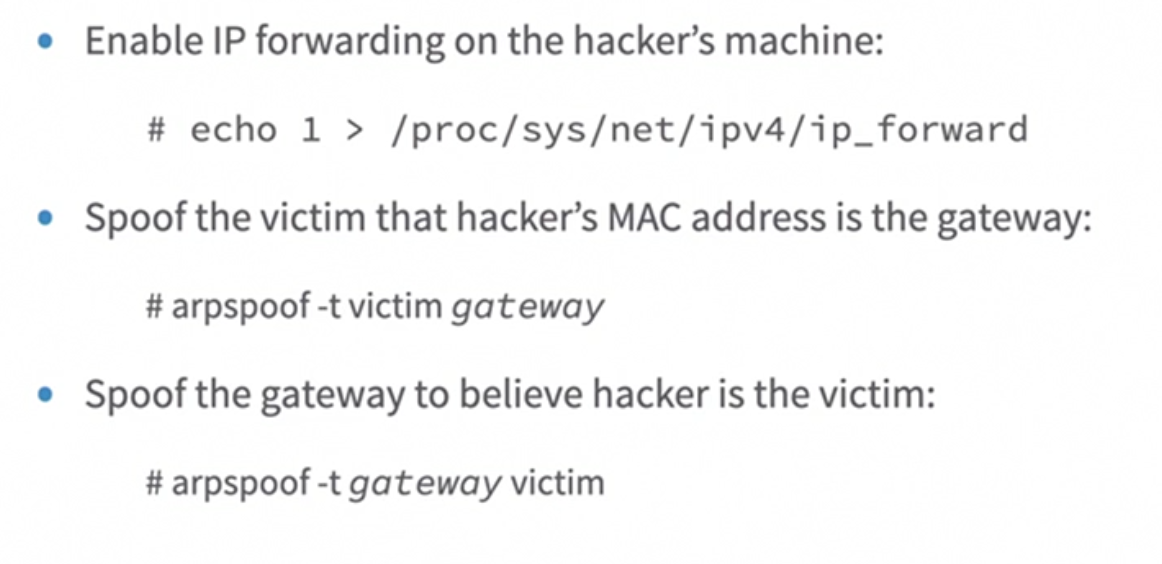
Over a LAN network, a device is identified by its MAC address. Changing the MAC address will allow an attacker to intercep traffic.

On linux we can perform this action by using the tool MACCHANGE
sudo macchanger -m 11:22:33:aa:bb:cc interface_name
Using another build in toll on Kali Linus we can spoof the ARP table
If attack is successful
Attacker will be able to launch a MitM attack and capture all traffic that the victim is sending to the router.
Nowdays most websites are encryoted with HTTPs, however, the attacker after capturing the traffic could decide to go a step further by decrypting the communication using methods like: SSLStripping , or SSL Downgrade in order to decrypt the attack.
Defending
Enable source guard on Cisco Switches. In order for the attack to bypass source guard, the attacker will have to spoof both MAC and IP addresses.
- Enable source guard on Cisco switches devices
- Consider using encrypted protocols always like HTTPS and SSH
- Avoid using file transfers like FTP and browsing websites on HTTP
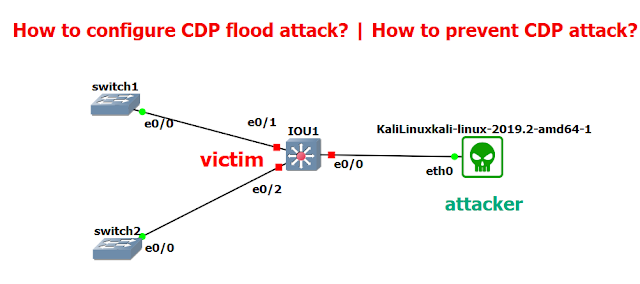
CPD Attacks
This is the Cisco Discovery Protocol that advertise other cisco devices, making it easier to find information on cisco devices likely IP Address,MAC,ports,OS, and running version.
If attack is successful
Attacker will be able to gather information about the network topology, device model #, version#, ports, switches, and more.
Defending
Consider disabling CPD Protocol, or turn it off on devices that are not needed, specially at the edge of your network.
STP Attacks
STP is a network protocol that ensures a loop-free topology for Ethernet networks. It prevents the formation of loops in the network by blocking redundant paths between switches, thus avoiding broadcast storms and network instability.
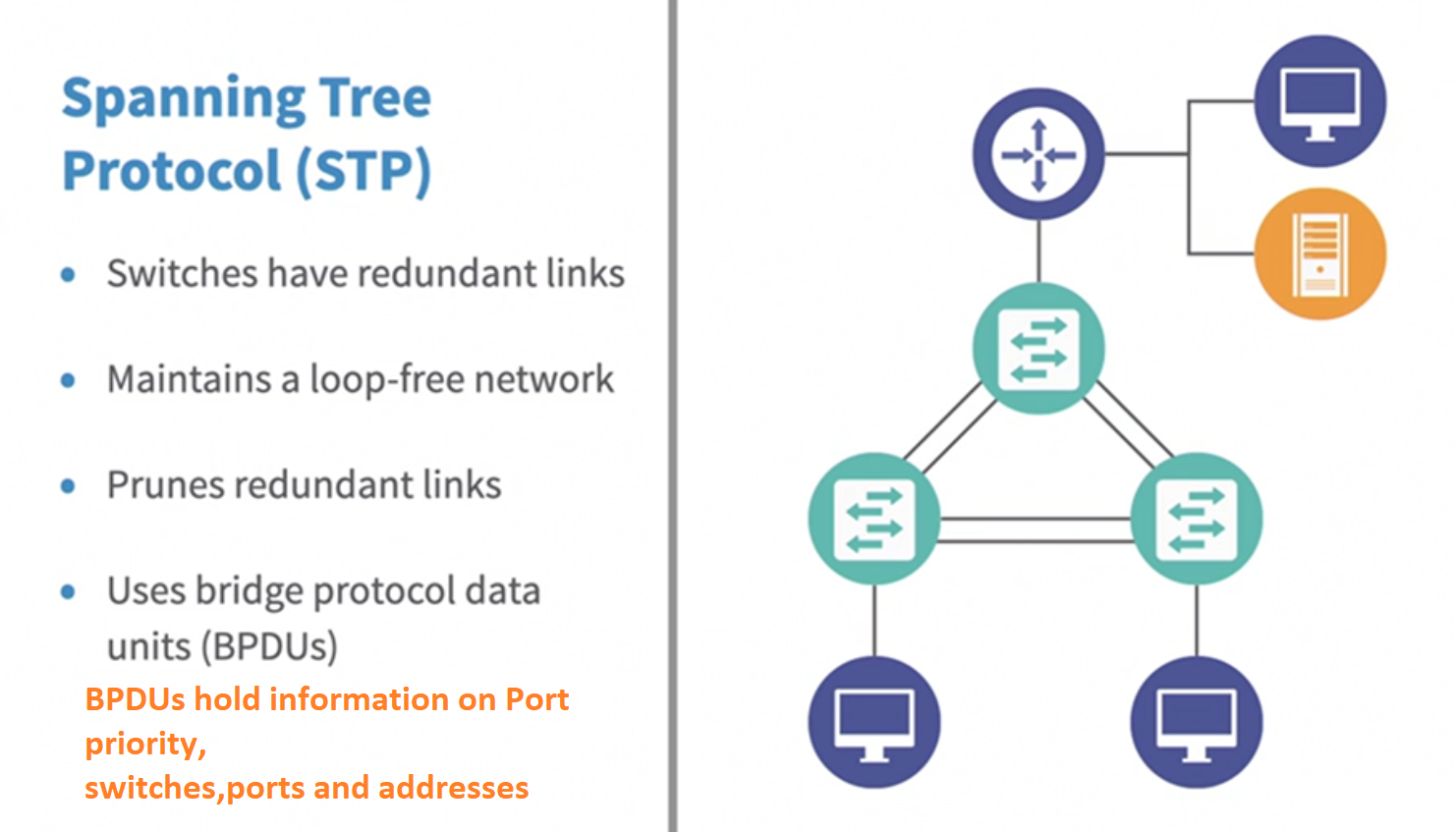
If attack is successful
Spanning Tree Protocol can be a target of DOS(Denial of Service) using BPDU flood, take over the root bridge or claim another role.
Defending
Enable PortFast, then configure BPDU guard. If we do have Spanning Tree active we can configure the port to stop receiving BPDU units (Bridge Protocol Data Units)

Do not disable completely spanning Tree or you will get a looping effect on your network causing a network storm.
VLAN Hoping Attack
User will spoof a swtich making his end device act as a trunk port
This can happen if the switch is set to auto-trunking or dynamic trunkig mode which is the default
If the port senses that is attach to a trunk line, it will change mode to trunk, this way letting the attacker see
all traffic across all VLANs

If attack is successful
Attacker will be able to steal passwords, deployed malicuos software across all network.
Defending
Disable dynamic trunking protocol on switches and configure the port to be an access port on a CISCO switch type the following
(config)#switchport nonegotiate
Verify configuration by running
(config)# interfce interface-id switchport
IRDP Spoofing
IRDP Protocol is similar to ICMP, and its used by routers for host discovery. Its used by routers to discover information abot other routers, it uses to discover informaton about other routers and learning about its configuration
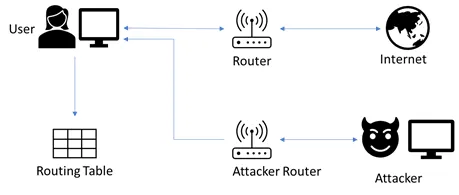
Attack
Attacker sends spoofed IRDP router advertisement message to the host on the subnet, causing it to change its default router to whatever the attacker chooses. Attacker is able to re-direct traffic from the router to his device, he can then itnercept, read, or modify the traffic or launch a more serious attack
Defending
- Configure routers to only accept packets from trusted sources
- Secure
- Consider disable router discovery
- Keep Router's software updated
Summary
These are some of the attacks that can be launched on Layer 2, there are more but we will have to leave them for another time. Hopefully this should give you some insight on what other methods we can implement to protect our network, stay tuned for more security tips
.png)