Load Balance and Azure
A load balancer is a networking service that distributes
incoming network traffic across multiple virtual machines (VMs) or backend resources,
ensuring efficient utilization and optimal performance.
Apart from reshaping traffic Load Balancers also enhance security by providing:
- Single entry point for incoming traffic
- Enabling the implementation of firewall rules
- Access controls
- SSL termination
When creating the Load Balancer it needs to belong to the same region the network you are attaching it to.
Quick Steps Summary
Below is a summary of the steps that you need to complete in order to launch a Load Balancer on Azure.
- Create Load Balancer within same region of network/resources
- Add VMs to backend pool
- Check for open Ports on NSG and VMs
- Create Health Probe to monitor server
- Crete rule to manage traffic
Load Balancers can route traffic internally and externally, if exposed to the internet.
⚖️ Azure Load Balance Terms
- What ports we are listening to
- Is it IPv4 or IPv6
- Which servers we sending to
Frontend IP Configurations
Private or Public IP. This setting will control If the Load Balance will be routing outbout traffic into the servers.
Backend pools
We have the option to link the load balancer to a Group of servers, or virtual machines
Health probes
The health probes are used to monitor the backend pool. Health probes checks if the server is up, to send traffic throught.
Load balancing rules
How we distribute the traffic within the backpols. This controls settings like:
We can set up an affinity settings, this will create a memory in the cache that will remember which server the user has access last and try to push it to him again.
Inbout NAT rules
This option is useful when we need to bind a specific IP/port to a specific instance in backend pool. We can map for example RDP to the IP of our load balancer on port 9988 for example, and the traffic will be re-directed to one of our Management VM inside the Backend pool to port 3389.
Outbout rules
Will control the outgoing traffic coming out of the servers.
Scale set Vs Availability set
There are two types of virtual machines in Azure, ScaleSets and Availablity Sets.
⚖️ Scale Sets will create and delete the virtual machines automatically, so load balancer is updated automatically.
💻 Availability Set create a unique set of VMs to be attached to the pool.The back end pool needs updated manually.
ScaleSet
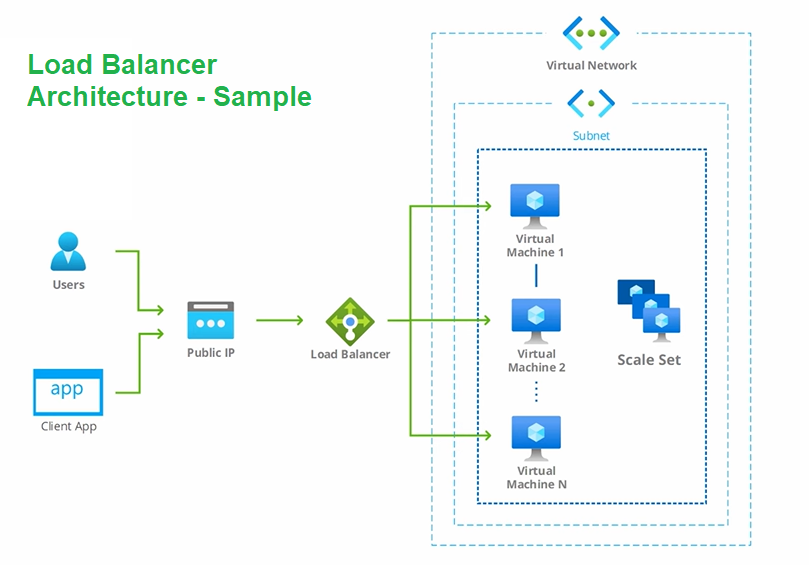
Scaleset is a group of identical Virtual Machines, this option is great if you want to distribute the traffic equally across the VMS throught the laod balancer. A scaleset is typically always located within the same subnet and network.
This group of VMs when combined will become the back end pool we going to use for our load balancer. In case of scale sets backend pool is updated automatically.
Availability Set
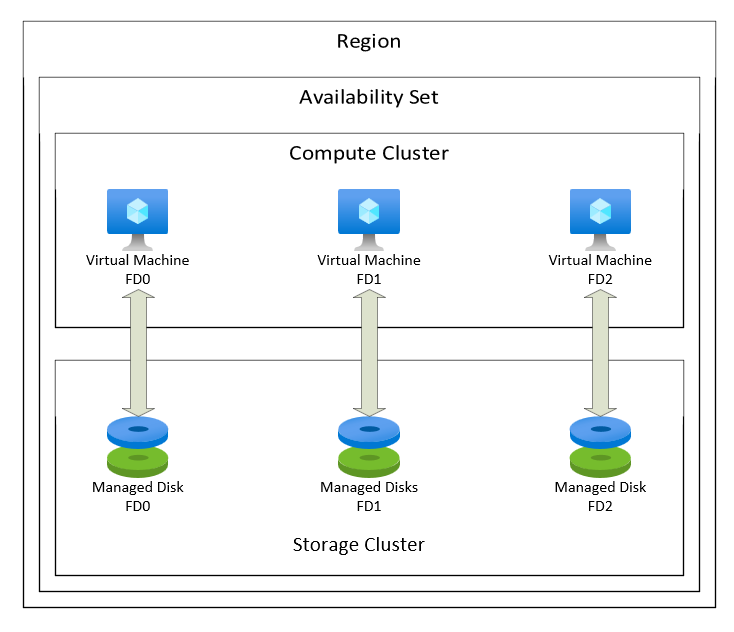
Availability sets are groups of VMs in Azure that reduce the risk of simultaneous failures. To leverage availability sets, create at least two VMs within the set. This guarantees application high availability and meets the 99.95% Azure SLA. Using availability sets incurs no extra cost, only charging for each VM instance. More info on Microsoft Documentation here
Azure Load Balance Tiers
There are a different levels of Load Balancer you can have on Azure below is a quick summary
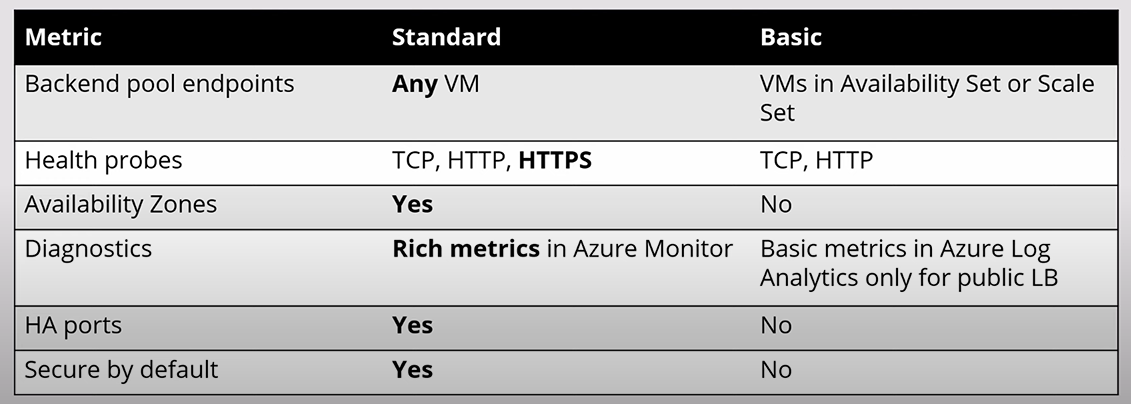
One main difference is that Standard is secured by default, which mean we have to open the ports on the Secutiy Group ourselves. In contrast, Basic will have the ports open by default.
Health Probe
A health probe is a way that Load Balancer will monitor the status of the servers. It will send a probe to check if the servers are up and running and report unhealthy if does not respond.
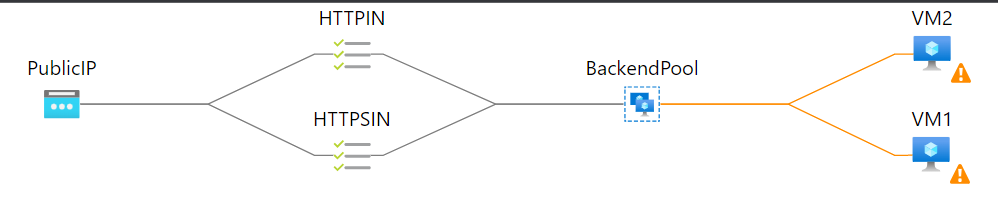
On the example above we have two servers that are running, however, the server only has the port 80 open, and because the Load Balaner is sending a probe to port 80(HTTP) and 443(HHTPS) it will report the servers as unhealthy.
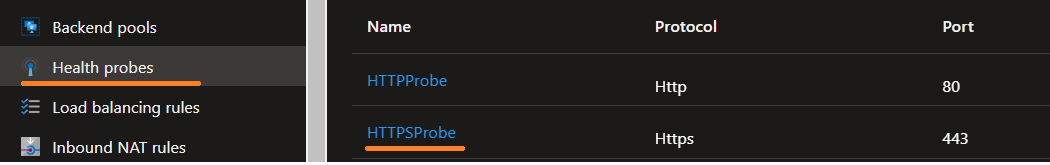
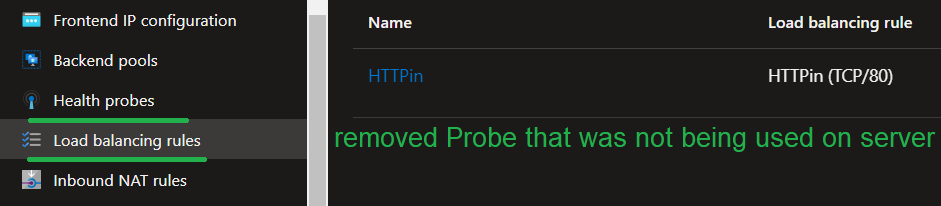
The solution is to either open the 443 port on the servers. or to remove the health probe that is causing issues. On this example we went with removed the probe.
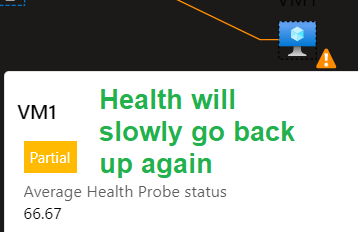
After removing the probe the health of the server will start go increase again.
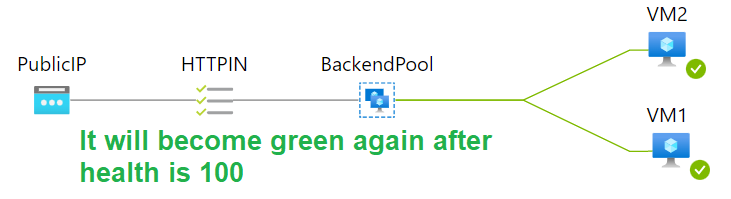
#
Load Balance Rule
The settings here are straight forward, and is the usual 5-Tuple It includes a source IP address/port number, destination IP address/port number and the protocol in use.
The session persitence if checked yes will make the user connect to the same server once the rule learns from the IP address he uses to connect for the first time.
Load Balancers vs Other Services

The way load balance difference from the other services from Azure is that Load Balance is designed for non-HTTP regional services. If we need to route traffic for a web application its recommend we use Application Gateway instead.
Azure Front Door and Traffic Manager works in a similar way but it was made to route traffic from a global scale.
If you are building an web application, you should be using Application Gateway as it has more settings to contol HTTP/HTTPS requests.
Good Topology
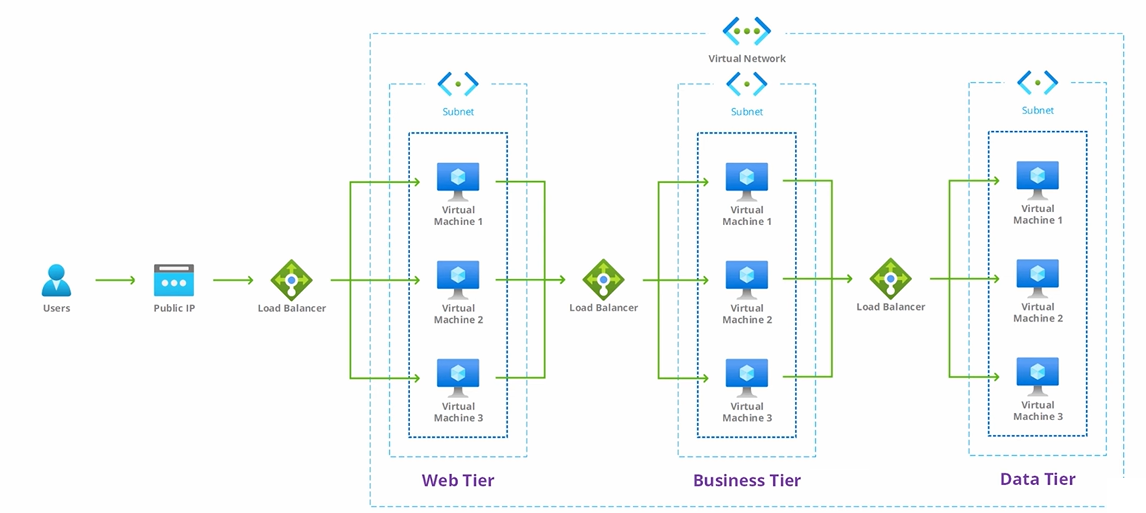
Having load balancers within both the Public and Local Area Network (LAN)
is crucial for ensuring proper traffic distribution and achieving optimal performance.
In the Public Network, load balancers distribute incoming traffic across multiple servers,
preventing any single server from being overwhelmed and ensuring high availability.
Similarly, within the LAN, load balancers distribute traffic among internal servers, preventing congestion,
optimizing resource utilization, and improving overall network performance.
This ensures that applications and services within the organization experience efficient load balancing, minimizing
latency, maximizing throughput, and providing a smooth user experience.
Thus, implementing robust load balancing topology both externally
and internally is essential for maintaining a reliable and high-performing network infrastructure.
.png)