Security Benefits of Docker
Docker is an open-source platform that allows you to automate the deployment and management of applications using containerization. It enables you to package an application and its dependencies into a standardized container, which can then be easily distributed and run consistently across different environments.
Docker containers provide a secure and isolated environment for applications, preventing conflicts and dependencies between different software components. Docker also provides built-in security features such as isolation, resource constraints, and network controls, helping to mitigate risks and reduce the attack surface for applications Amongst other benefits like . There are many benfits in using docker when on your enviroment, these include:
- Isolation
- Reproducibility
- Scalability
- Security Hardening
- Rapid Recovery
- Microservices Architectur
WTH is Docker? 🐳
The official docker website you will find a guide on how to install docker
We are going to have a quick look on how to install docker on Linux and some commands to create, manage launch and dispose an image.
Installing Docker
TO install docker you want to make sure your system is up to date with
git apt update && git apt upgrade
Once your system is fully updated you can install docker by runnin:
sudo apt install docker.io
Installing Dependencies
As every other software, docker has a dependencies library which is great to install them now to avoid any conflict in the future. To install the dependencies fo docker run:
sudo snap install docker
Verifying installation
Verify everythig has worked by running docker --version Also a good way to check if all is working correctly is to download an image directly from docker and see if that works correctly. On the Docker Oficcial website there is an image library each with a pre install applications you can use, like images with python, npm, SQL Libraries etc..
We are going to pull an image named hello-world which is pretty much a test image used for testing everything is working well.
sudo docker run hello-world
Show Available images
You can view the available images on your system by running
sudo docker images
Show Running Images
To see all your running containers you can run the following
sudo docker ps
Show all images running and also images that are offline.
sudo docker ps -a
Create a new Container
Writting Docker Instructions
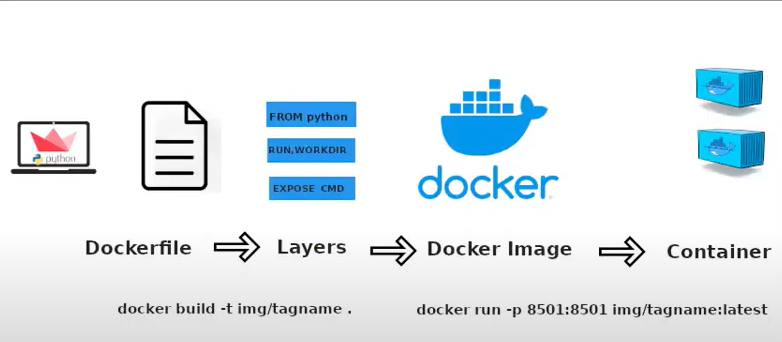
To create a new container you will have to create a Dockerfile
This docker file has a set of instructions which are used to build your image. Imagine the instructions being something like:
Create a folder 📁
move fila a to ./
install nginx
change config on nginx to xx
python main.py 🐍
Here is an example of an actual Dockerfile
FROM python:3.9 WORKDIR /app COPY requirements.txt ./requirements.txt RUN pip3 install -r requirements.txt EXPOSE 8501 COPY . /app ENTRYPOINT ["streamlit", "run"] CMD ["main.py"]
The file must be called Dockerfile
Creating Docker Image
After your Dockerfile is created you can run the following command to turn into an image.
sudo docker build -t myCoolApp .
The . indicates you are looking for the docker file inside the current folder, so make sure the Dockerfile is on the root folder of your application
Altenativally you can also run the following if you have named your Dockerfile something else like, image.dev or image-prod
sudo docker build -t myOtherApp -f ./folder/Location/Dockerfile
If you encouter an error during the creation of your docker, make sure you are running a system that has enough
memory.
Another common issue is misplacing the file on a different location, or not naming it properly.
Running a Container
After you have created the image you can launch it by runnign the following command. The first port is the port that you are exposing on your network, the second port is for the PORT info that you have set up inside the Dockerfile when writing it.
sudo docker run -p PORT:PORT myCoolApp
When launching your container any environment variables on your project will need to be passed during the moment you run the container. use the below code as an example
sudo docker run -d -t -i -e REDIS_NAMESPACE='staging' \ -e POSTGRES_ENV_POSTGRES_PASSWORD='foo' \ -e POSTGRES_ENV_POSTGRES_USER='bar' \ -p 80:80 \ --link redis:redis \ --name container_name dockerhub_id/image_nameSource: StackOverFlow
Accessing a Container
This command is used to access a runnig container
docker exec -it container_id bash
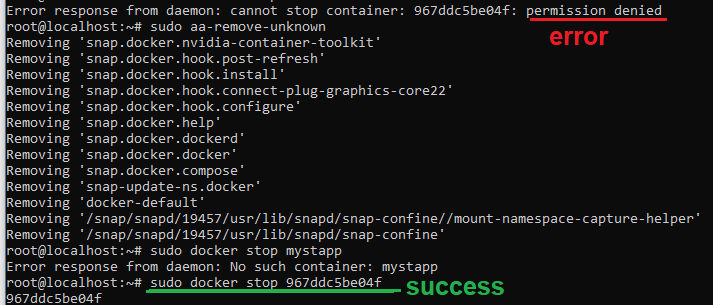
Deactivate a Container
To deactivate a Docker container, you can use the docker stop command followed by the container's ID or name. This command sends a signal to the container, requesting it to stop gracefully. Here's the basic syntax:
docker stop container_id
Error: Response from daemon:cannot stop caontainer: hash_id_num: permission denied.
To fix this error you need to run the following command
sudo aa-remove-unknown
Soft Deleting a Container
This is used to delete a stopped container, and its a soft delete. Deleting an image this way will not delete the cache on your computer This is useful if you need to rebuild the image with some modifications.
To check your current docker containers you can run the below
sudo docker ps -a
After deciding which image you will demove, you can run the below to remove the container
docker rm container_id
Hard Delete image
This commnand will compeltelly remove the container from your local drive, if you build the image again it will computer everything from scratch.
Check the curernt images on your system by running
sudo docker images
You can then run the below command to remove the image completelly from your system.
docker rmi container_id
In case you are having trouble deleting you can force delete simply by adding the -f
Final thoughts 🎆
Congratulations , you now have a running Docker application!
By containerizing your application with Docker, you've improved security.
Docker isolates applications in individual containers, preventing conflicts and limiting
the impact of breaches.
Reproducible images ensure consistency and simplify updates. Scalability
allows efficient resource allocation and reduces denial-of-service risks. Embracing microservices
architecture enhances security by isolating vulnerabilities. Docker integrates seamlessly with CI/CD,
enabling automated security testing and quick rollbacks.
Its lightweight deployment and fast recovery in addition it has built-in security features,
like resource constraints and network controls,further strengthen application security.