What are Data Streams?
Okay, so you might not have heard about NTFS file streams before,
but they're like secret hideouts inside your Windows computer.
This blog post is all about how sneaky hackers use these file streams
to hide their actions when they're up to no good, and it will also show
you how to protect your computer.
Think of a file stream as a hidden room inside a regular room.
It holds important information about a file, like keywords or who made it.
Each stream has its own special space, size in bytes, and locks.
Every file in your computer has at least one stream called the default stream.
This is the regular stuff you see when you open a file, like the text in a .txt
file or the code in a .exe file. This default stream is stored in something called
the $Data attribute. It's kinda funny because it doesn't even have a name –
it's often called the "unnamed data stream."
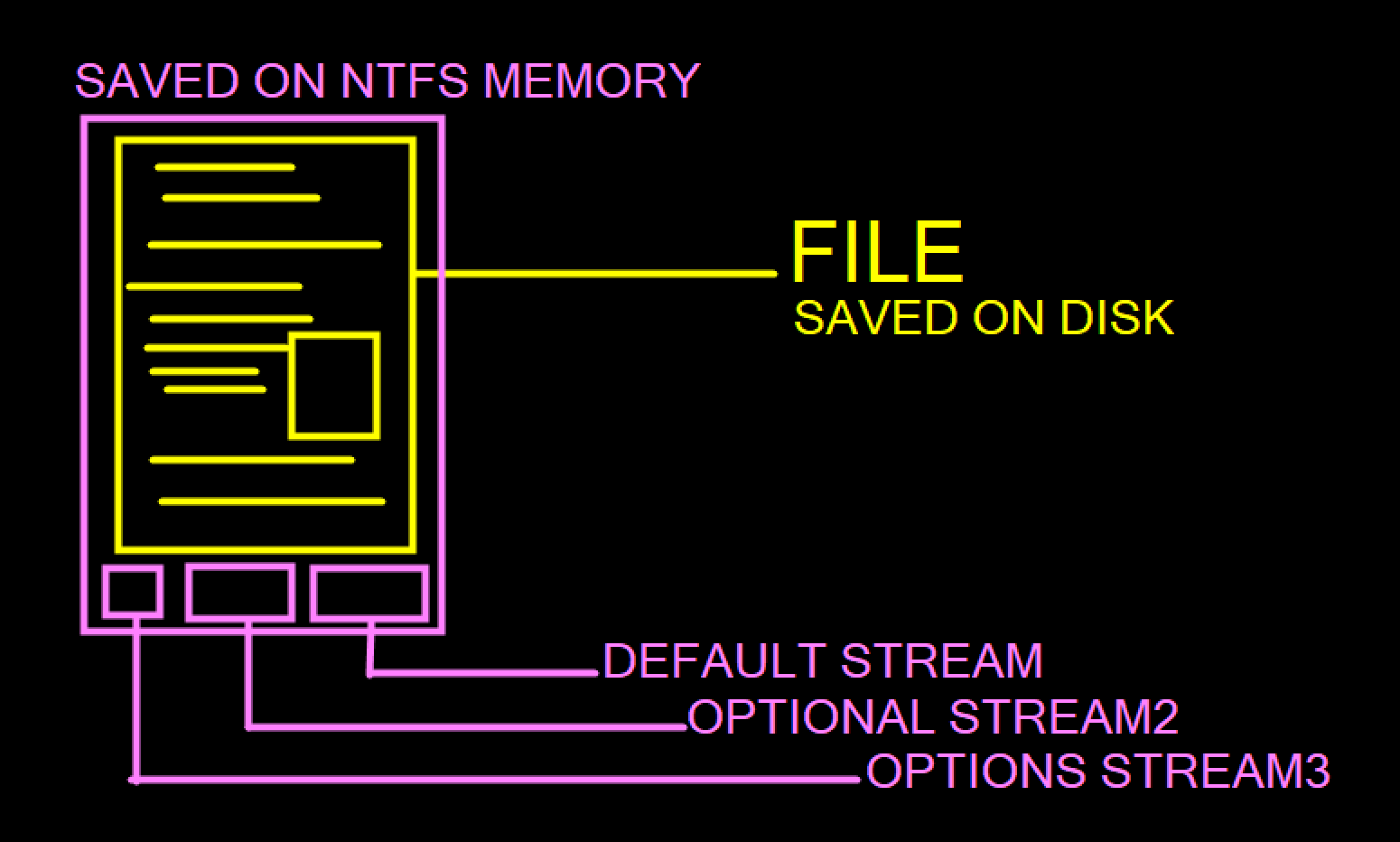
But guess what? Files can have more secret streams, too, and these streams
must have names. What's really cool is that even if you add these secret streams,
the regular stuff in the default stream doesn't change. It stays hidden
and doesn't give away its secrets.
Data stream on AD NTFS System
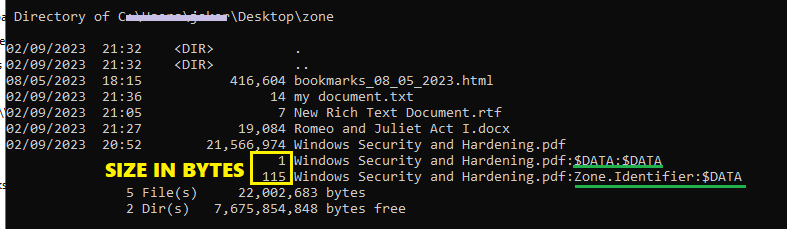
This protocol is being used by legit files to perform operations across the computer they would normally have metadata about the file itself, example below show a legit file using the data stream.
I have used the command dir /r to get the output file below.
How attackers are using data streams
When the files are downlaoded from the internet the data stream is removed from the file. However, Attackers are using this technique to hide their presence after they have ran the initial payload!. The below command will add the command ipconfig into the data stream of my.file.txt
echo ipconfig > myfile.txt:stream

IDS - Detecing data stream Injection
There are a few ways we could potentially spot this type of attack being used across our network, injecting code into the file stream is not common and should definitelly be taken as a high alert when you see a file is using some of the below commands.
- fileName:
- processName:
The : is important when doing this type of search, but the real power of this search is when you combine multiple IoC (Indicadors of Compromise) together to create the search query.
How to detect data streams
There are a few ways to detect data streams on a file, and unfortunatelly all of them include the command line. You can use the built in command on Windows we have talked about.
dir /r
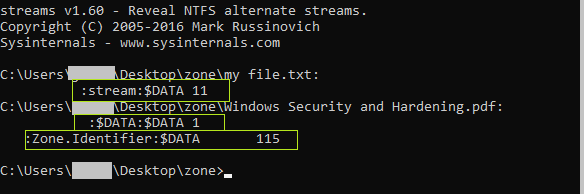
But the recommend tool for te job is call streams from SysInternals Windows tools.
I am using the * flag which will search for all the files inside the directory I am in.
For more information on the tool and other flags click here
streams *
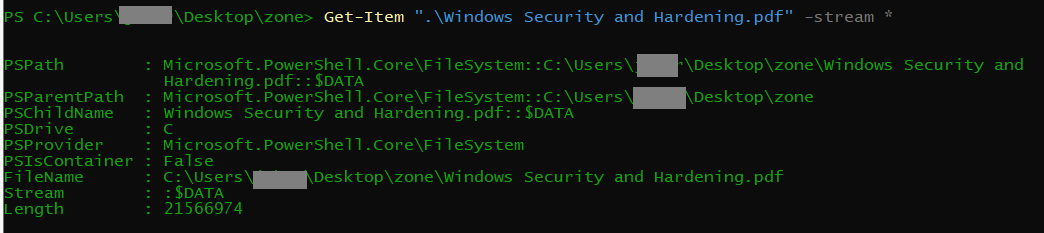
We can now (finally) detect streams using powershell Good luck finding a way how to read its contents using powershell.
How to read a data stream
It can be a bit tricky to read the stream, maybe because nobody needed to? Anyways, below is the command you need.
more < "Windows Security and Hardening.pdf":Zone.Identifier:$DATA
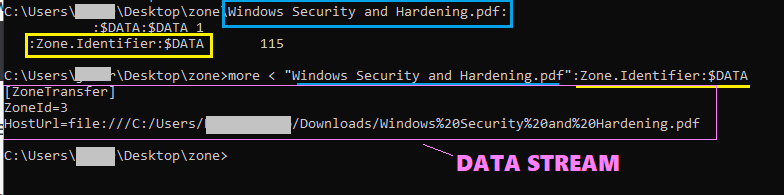
The command below will only work with cmd not powershell.
How to create a data stream
The command below will create a data stream into a file, you can also have multiple data streams. Data streams will be saved in memory, so they will not take any space into a file at all!, you could potentially save the entire Romeo and Julie play into the data stream of a file without changing the file size on disk of that file.
echo ipconfig > "my file.txt":secretStream

I am using " " between my file names because the file has a space in between, if you file does not have spaces you can type its name without ""
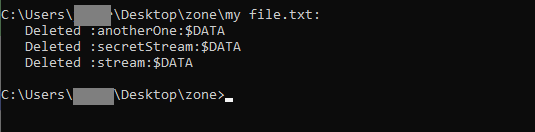
How to remove a data stream
We can remove the streams using the streams SysInternals tool command we mentioned above.
streams -d "my file.txt"
How to stay protected
The best way to stay protected is the basics which you probably are already familiar.
Conclusion
In conclusion, data stream attacks in NTFS systems are a real threat, but with vigilance and the right security practices, you can protect yourself and your system. Stay informed, keep your software updated, and use trustworthy security tools. Thank you for watching, and stay safe online!
.png)