Ransomware SUCKS!
.png)
On this post we will be looking into a few methods that can help us detect different stages of a ransomware attack, and what methods we can implement to monitor for these IoC(Indicators of compromise).
Ransomware has changed over the last few years, and now there are many groups who solely focus in creating the Ransom, while 'affiliates' or subscribers utilize the plataform to launch the attack, this is known as RaaS (Ransom as a Service).
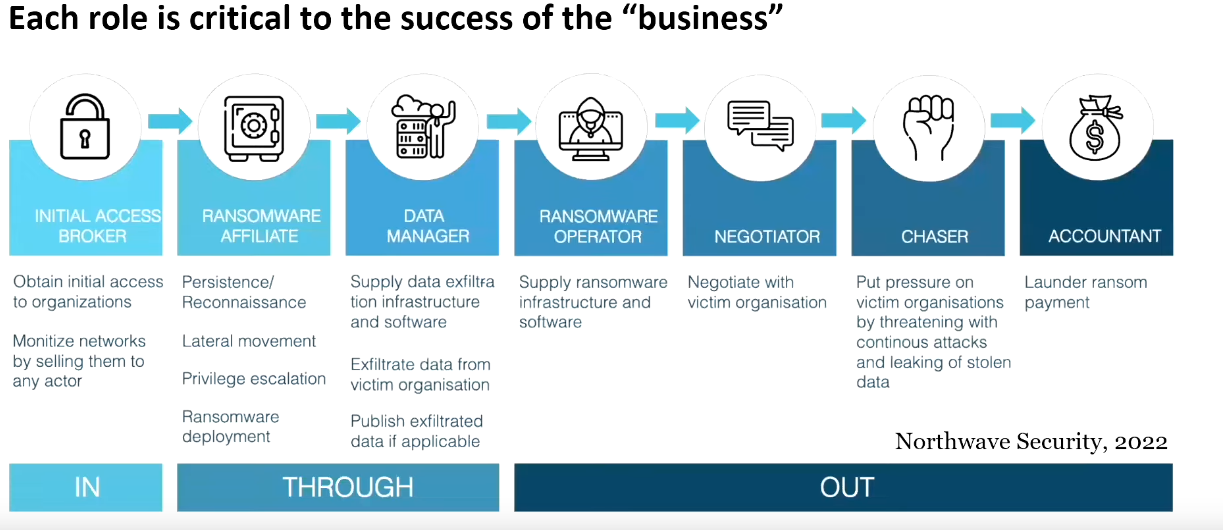
The image below is the attack flow a ransomware normally follows, understanding the different parts of the attack will help to place differente security measurements in place, thus helping our defense in depth.
Backup, backup, backup...
The number one method that you should already be using is backup, do it often, and test if frequently. Also have your backups stored offline if possible.
Consider using immutable backups, these are literally backups that will not change once they are created.
Understand your adversary
To undertand how to defende you need to understand what you are fighting against! The document "Cobal Strike Manual V2.pdf" was distributed by a RaaS group to their affiliates. The document expain steps on how to compromise the domain, steal documents, launch the encryptor and get out!
If we are understand the commands the attackers are using, we can do the exact opposite and place rules to help us defend against them. Use the Cobalt Strike Manual to identify what commands you can start monitoring on your organisation.
1st Phase - Initial Access
The initial access could hapen by brute force, or an insider could sell credentials on the dark web, be black mail in order to provide initial access, amongst other methods. Below are a few examples.
- Phishing
- Credential Stuffing /Re-use RDP
- Web Shell or Loader
- Exploitation
- Black Mail
Consider disabling powershell for users who do not need them, you can do this by methods of GPO, Intune or using JEA(Just Enough Administration).
If the attacker is not able to use powershell, the chances are his campaign will likely be a flop!
For a bit more information on the above check my previous post on Hardening our windows environment
To help reduce the intrusion on the initial access phase, we can implement E-mail defense mechanism, perform security audits on our environment, revise our policies frequently, and teach our users about phishing, and our developers on security best practices.
2nd Phase - Recon and Lateral Movement
These are some of the common tools used during an ransomware operation, these are often download from the internet or github repo,
often they would not even be renamed.
Monitor the download and usage of the below apps
- $COMSPEC% /c [command] (ie: cmd.exe)
- ADrecon
- Ping Castle
- WMIC
- MetaSploit
- ADFind
- Lazagne
- Bloodhound
- PowerSploit
- Mimikatz
- Netcat
- Advance IP Scanner
- LOLBins
- Process Hacker
- GMER
- TDSSKiller
- Hitman Pro
Monitor the url where the tools are being downloaded from, or possible block the urls when possible. ie: AnyDesk download link is : 'https://anydesk.com/en/downloads' - Can you block it? Can you monitor when its visited?
Detection against renaming of files
Even if the attacker rename the files before they download into your environment ie: TeamViwer.exe to funGame.exe, there are certain elements of that executable that will remained untouched during the compiling time and run of the application. So we can still monitor for the Original File Name on our EDR or on our XDR logs.
If we also have Sysmon deployed on our environment we can monitor for Event #1 - Process Creation and look for Original File name.
The resource below shows a map of the original file name and the executable name and can be useful to help create detections against certain tools. Velociraptor-Detecions/ExeOriginalFilename
Security Bypassing Techniques
Eventually, what the attackers want is to disable your security system so he can deploy whatever payload without being stopped. The below list is some applications which have been detected in real cases (but not limited) that are used to disable AV / EDR software.
Other Advance Techniques
They can also exploit an already vulnerable application you have running on your system by methods of DLL Hijacking or DLL Proxying
- BYOVD - Bring Your Own Vulnerable Driver
- DLL Hijacking
- DLL Proxying
- LOLBAS
Security Tools Disablers
Monitor the download and usage of the below software
- GMER | gmer.exe
- HitmanPro.exe
- PCHunter.exe
- ProcessHacker.exe
BYOVD - Bring Your Own Vulnerable Driver
Attacker can bring theirn own vultable drivers into the operating system, in order to bypass security already in place. The drivers below have been signed by Microsfot and are vulnerable so they can unload your current AV protection system.
Some of drivers abused by Ransomware TA to kill AV/EDR's
- gdrv.sys (Gigabyte) > RobinHood
- Hash: 9ab9f3b75a2eb87fafb1b7361be9dfb3
- aswArPot.sys (Avast) > CUBA and AvosLocker
- Hash: a179c4093d05a3e1ee73f6ff07f994aa
- mhyprot2.sys (Genshin Impact) > Rever
- Hash: 4b817d0e7714b9d43db43ae4a22a161e
Detecting LOLBIN (Living of the Land)
Threat actors will use the tools already in place on your environment to avoid detection. A lot of these are already part of the Windows system, so they don't need to download anything special.
To have a more indepth look into some of them follow this link for LOLBins
Monitor Remote Control Apps
Try to implement on your organisation only 1 remote access app, ie: Team Viewer, or ScreenConnect. If you Microsoft-System-Center-Configuration-Manager-2012
to establish a white-list for the remote access apps that are allowed to be used on the environment, you can place detections in place
that would pick up any other not authorised use of a remote access app like, AnyDesk, Splashtop, Atera, etc..
Monitor for the use of the below apps.
- Remmcos
- Zoho Assist
- Parsec
- Remote PC
- VNC Connect
- GoToMyPC
- LogMe In
- ISL Online
In case of compromise is detect using any of the Remote Access Applications, check for their logs as you will often be able to discover, IP addresses,file transfer, and other artifacts.
3rd Phase - Data Exfiltration
Once they have discovered your environment and your data, which on this step could happen between a few hours after the initial
compromised, or a few weeks. The next stage is to get this data away from your server and into the attackers server.
Their method of choice
will depend on what you alread have in place on your environment, this is to avoid them from being detected after all,
you alread have 'all exlusions' and their exfiltration is likely to be overlooked if you do not have the correct DLP Policies in place
Monitor for download & upload to the following websites
- Also check LOTS project exfiltration section
- Anonfiles.com
- dropmefiles.com
- file.io
- mega.io | mega.nz
- qaz.im
- temp.sh
- termbin.com
- transfer.sh
- keep.sh
- ufile.io
- StealBIT
- 7-ZIP
- WinSCp/FileZilla
- Rclone
- Rsync
- MEGASync
The website www.keep.sh is one example of website commonly used by threat actors where they can download and upload files straight from the command line.
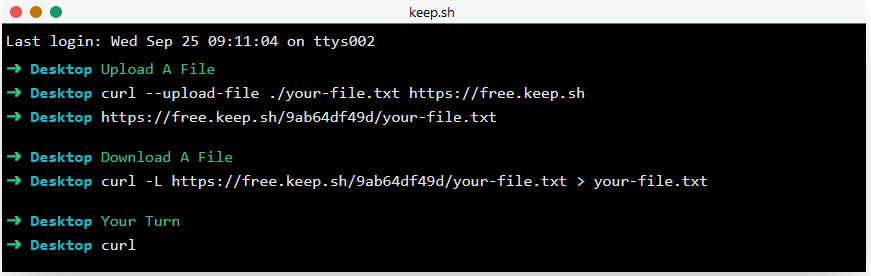
Data exfiltration can also happen over DNS queries, to help detect those we will need to monitor Firewall logs, and DNS Server logs.
4th Phase - Ransom Deployment!
Threat actors will often use what you already have implemented on your environment to distribute the payload, this could one of the following below.
- AD Group Policy
- Intune MDM (Mobile Device Managemen)
- PSExec
- SCCM
- Manage Engine Endpoint
Detecting PSExec
Below is an image of some of the methods we can use to monitor PSExec usage.
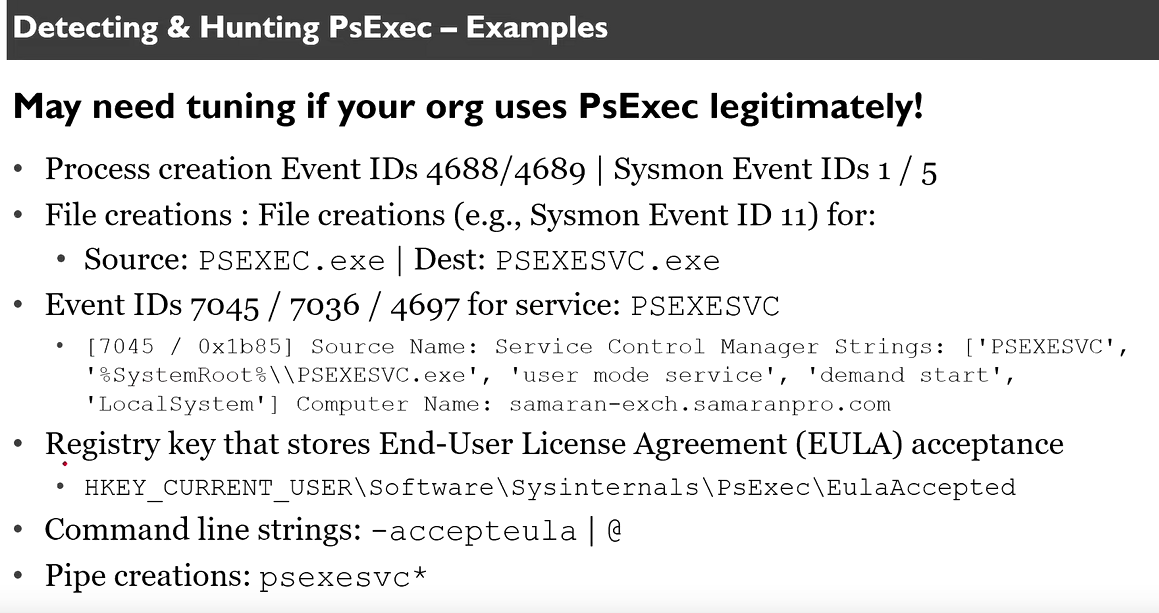
On our XDR/EDR system we can monitor for Event ID (4688,4689, 7045,7036,4697), perform some test on the environment yuorself to refine the filters.
Tools Offload Locations
There are certain folders on Windows that have Read,Write,Execute access by everyone, this is part of the OS but often these are the location where malware will be uploaded to be later executed into the system. Monitor these locations for any suspicious files.
Below are some of the locations threat actors commonly used for staging.
- %AppData% | %ProgramData% | %TEMP%
- REGEX: C:\Users\Public
- REGEX:C:\Perflogs\
- Monitor for suspicious EXEs in %AppData% & $LocalAppData%
- REGEX: C:\\Users\\.+\\AppData\\(Roaming|Local)\\.*\.exe
- Monitor for EXEs dropped into these directories
- REGEX: C:\\ProgramData\\.+\.exe
- REGEX: C:\\Users\\Public.*\.exe
- %UserProfile% locations
- REGEX: %USERPROFILE%\\(Videos|Music|Pictures)\\.+\.(exe|dll|bat|ps1)
- %COMSPEC% /c [command]
- REGEX: ^.*COMSPEC.*echo.*pipe.*$
- See also WinSxS,$Recycle Bin,& Temporary Internet Files directories
If you can hunt on your environment for %COMSPEC% , its a huge red flag as this is not a common way to call cmd.exe.
Summary
The idea of this article is not to show you all possible IoC that can happen during the ransomware phases, but simply to show you a few examples, and hopefully demonstrate how you can find more information to create more tailor detection model for your company.
.png)